This article gives you basic information about ELAM Solutions own hosting and its system requirements. At the end of this article you will find an example configuration for an OnPremise Network.
The ELAM Solutions software can be installed on a server that supports at least MicroK8s (a lightweight Kubernetes distribution) in version v1.28.3. Linux (Ubuntu 22.04 or higher) is required as the operating system.
Note: Windows Server can be used with a HyperV.
To ensure the successful installation and maintenance of our software solutions, a continuous internet connection is required on the server at the installation and update time.
After that the System can be run offline without internet access.
Minimum hardware requirements are based on the number of stations used in ELAM Solutions.
A solid-state drive (SSD) with a minimum capacity of 100 GB is required. Storage consumption will increase over time as data and images are stored in the system.
The complete installation package for ELAM Solutions is made available in an Azure repository. The installation package is loaded from the repository and installed on the server. An active internet connection on the server is required for this process.
For the installation of ELAM Solutions On-Premise software, a server certificate, a key file, and the root certificate are needed. These are essential to ensure secure (encrypted) communication between the server and the client.
In this context, the configuration and use of SSL/TLS certificates for secure communication on a server are described. Here is an explanation of the terms:
1. Server Certificate (.crt):
This is the SSL/TLS certificate specifically issued for the server. It identifies the server and is used to establish a secure connection (e.g., HTTPS). It contains information about the server, the domain name, and the public key used for encryption.
2. Key File (.key):
The .key file contains the server's private key. This key is used together with the public key (in the server certificate) to decrypt encrypted data traffic. The private key remains on the server and is not made public.
3. Root Certificate (.crt):
The root certificate is the certificate issued by a Certificate Authority (CA). This certificate is used to verify that the server certificate comes from a trusted source. The client uses the root certificate to verify the server's identity. In many cases, the root certificate can be combined with intermediate certificates to form a certificate chain.
What is a Certificate Chain?
A certificate chain is a sequence of certificates that build upon each other to establish trust in a certificate. The chain starts with the server certificate and ends with a trusted root certificate. In between, there may be intermediate certificates that transfer the trust from the root CA to the server certificate. This structure allows trust to be built step by step.
Example of a Certificate Chain:
The following addresses and ports must be enabled for installation on the server:
Helm charts are used for installations or updates. A Helm Chart is an installation package for Kubernetes applications. It enables the installation, management and updating of ELAM Solutions software in a Kubernetes cluster.
In order for e-mails to be used for user logins, parameters of an e-mail server must be provided so that the ELAM Solutions On-Premise software can send e-mails.
List and explanation of the individual parameters:
To connect a SmartTower to your on-premise instance, a certificate must be generated and configured for the tower. This certificate must match the certificate of the on-premise instance. Once configured, the SmartTower can be added according to the instructions in the Help Center.
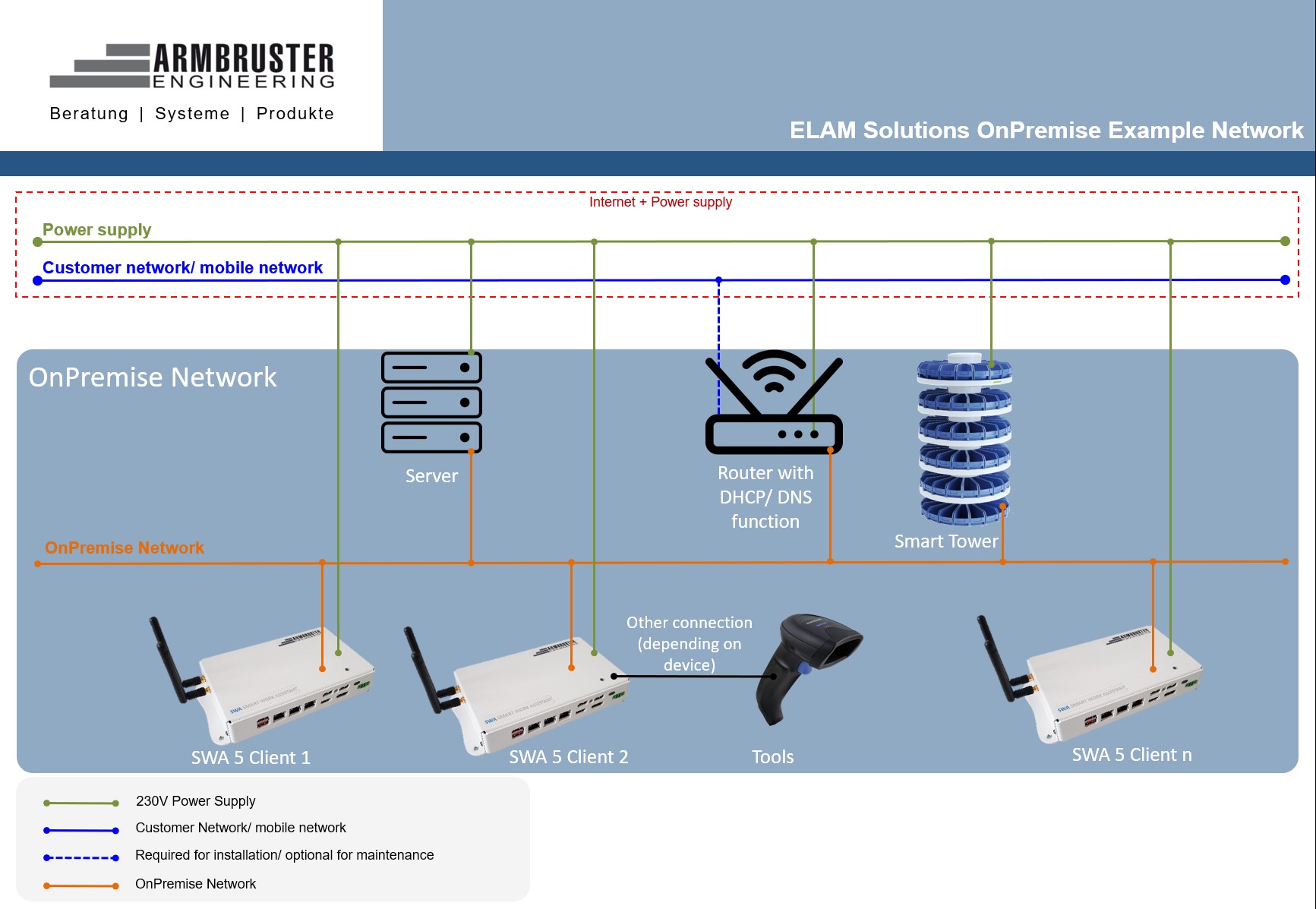
In the following you will find an example configuration for an OnPremise Network.